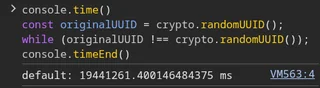
brother you're using the wrong thing. First of all you are using crypto that's going to give you some memecoins that are obviously going to collide after 55 hours as what are you even doing not rugpulling the thing day 2?
Second of all, I am pretty sure you should use "RandomUUIDIToldYouSo" module for non-colliding hashes. We all know THAT thing gets its Noise from our parents' instructions on doing a specific thing that keep changing arbitrarily every time you ask.