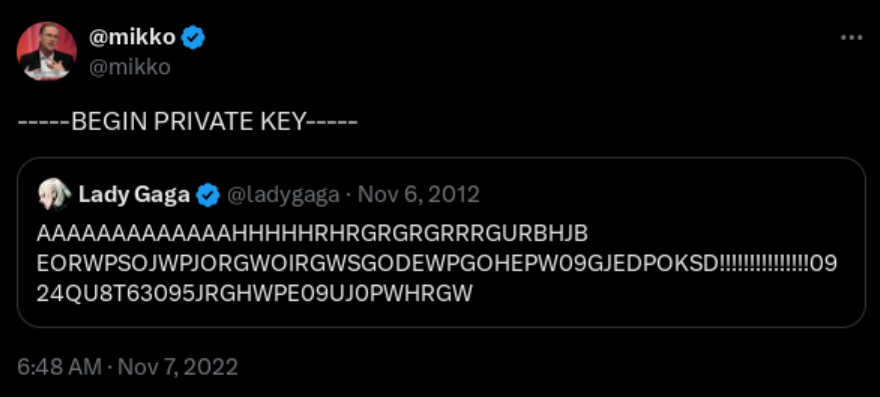
Replying to a 10-year-old tweet is a power move in itself.
linuxmemes
Hint: :q!
Sister communities:
Community rules (click to expand)
1. Follow the site-wide rules
- Instance-wide TOS: https://legal.lemmy.world/tos/
- Lemmy code of conduct: https://join-lemmy.org/docs/code_of_conduct.html
2. Be civil
- Understand the difference between a joke and an insult.
- Do not harrass or attack users for any reason. This includes using blanket terms, like "every user of thing".
- Don't get baited into back-and-forth insults. We are not animals.
- Leave remarks of "peasantry" to the PCMR community. If you dislike an OS/service/application, attack the thing you dislike, not the individuals who use it. Some people may not have a choice.
- Bigotry will not be tolerated.
3. Post Linux-related content
- Including Unix and BSD.
- Non-Linux content is acceptable as long as it makes a reference to Linux. For example, the poorly made mockery of
sudoin Windows. - No porn, no politics, no trolling or ragebaiting.
- Don't come looking for advice, this is not the right community.
4. No recent reposts
- Everybody uses Arch btw, can't quit Vim, <loves/tolerates/hates> systemd, and wants to interject for a moment. You can stop now.
5. 🇬🇧 Language/язык/Sprache
- This is primarily an English-speaking community. 🇬🇧🇦🇺🇺🇸
- Comments written in other languages are allowed.
- The substance of a post should be comprehensible for people who only speak English.
- Titles and post bodies written in other languages will be allowed, but only as long as the above rule is observed.
6. (NEW!) Regarding public figures
We all have our opinions, and certain public figures can be divisive. Keep in mind that this is a community for memes and light-hearted fun, not for airing grievances or leveling accusations. - Keep discussions polite and free of disparagement.
- We are never in possession of all of the facts. Defamatory comments will not be tolerated.
- Discussions that get too heated will be locked and offending comments removed.
Please report posts and comments that break these rules!
Important: never execute code or follow advice that you don't understand or can't verify, especially here. The word of the day is credibility. This is a meme community -- even the most helpful comments might just be shitposts that can damage your system. Be aware, be smart, don't remove France.
this is gold yet I don't know anyone who would get it that I can share it with
I just shared it with a bunch of people while also telling them that I didn't care if they didn't get it and I wasn't going to explain it.
They're used to this.
Edit: 2 of them got it. That's pretty good for me. I've played to smaller crowds.
That's why we come to the internet. Real life people suck.
That’s why I have a sister studying cyber sec 😎
I shared it to the memes group at work, as a developer
I have exactly one person and they loved it.
If you had to explain it, how would you?
It's sad that I can't find anyone to share this with.
I have literally one friend who would get this, and I try not to bombard him with memes, as I can tell it gets on his nerves sometimes, even when he thinks it's funny.
I'm in your exact camp.
I share these with friends who might not get it. It's like a UDP joke
ACK
NAK
␆
As long as you gave your best effort.
I wonder if you string together enough words can it be a valid key?
I would hope so, sentences and words are some of the most secure passwords/phrases you can use
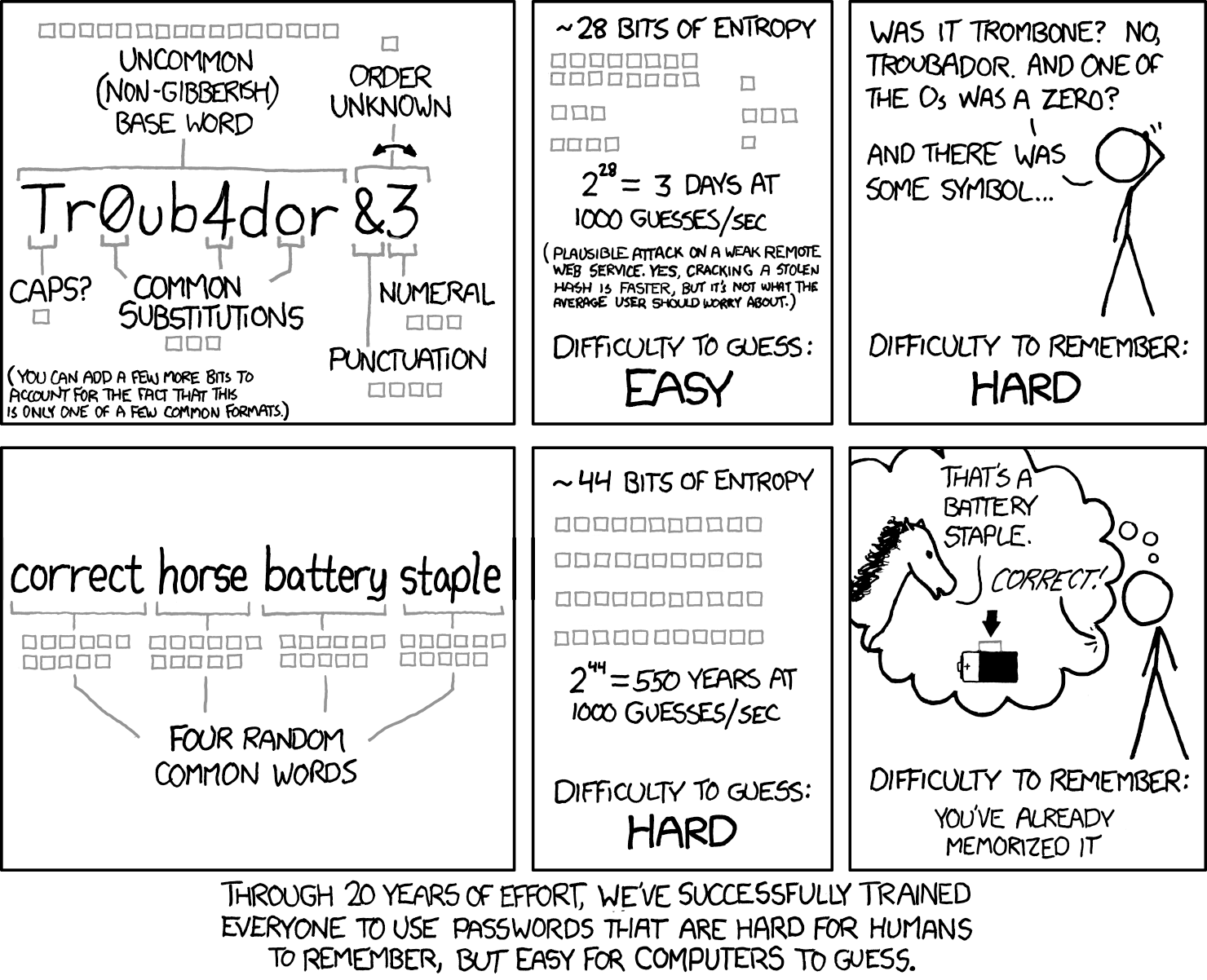
Words are the least secure way to generate a password of a given length because you are limiting your character set to 26, and character N gives you information about the character at position N+1
The most secure way to generate a password is to uniformly pick bytes from the entire character set using a suitable form of entropy
Edit: for the dozens of people still feeling the need to reply to me: RSA keys are fixed length, and you don't need to memorize them. Using a dictionary of words to create your own RSA key is intentionally kneecapping the security of the key.
That's only really true if you're going to be storing the password in a secure vault after randomly generating it; otherwise, it's terrible because 1) nobody will be able to remember it so they'll be writing it down, and 2) it'll be such a pain to type that people will find ways to circumvent it at every possible turn
Pass phrases, even when taken with the idea that it's a limited character set that follows a semi predictable flow, if you look at it in terms of the number of words possible it actually is decently secure, especially if the words used are random and not meaningful to the user. Even limiting yourself to the 1000 most common words in the English language and using 4 words, that's one trillion possible combinations without even accounting for modifying capitalisation, adding a symbol or three, including a short number at the end...
And even with that base set, even if a computer could theoretically try all trillion possibilities quickly, it'll make a ton of noise, get throttled, and likely lock the account out long before it has a chance to try even the tiniest fraction of them
Your way is theoretically more secure, but practically only works for machines or with secure password storage. If it's something a human needs to remember and type themselves, phrases of random words is much more viable and much more likely to be used in a secure fashion.
Generally people don’t memorize private keys, but this is applicable when generating pass phrases to protect private keys that are stored locally.
Leaving this here in case anyone wants to use this method: https://www.eff.org/dice
Edit: Oops forgot what the topic was.
-
we are talking about RSA keys - you don't memorize your RSA keys
-
if you rely on memorizing all your passwords, I assume that means you have ample password reuse, which is a million times worse than using a different less-secure password on every site
Derp. Forgot where I was.
I find passphrases easy to remember and I have several. I appreciate the concern, but I understand basic password safety.
Good luck remembering random bytes. That infographic is about memorable passwords.
You memorize your RSA keys?
you memorize the password required to decrypt whatever container your RSA key is in. Hopefully.
so you are saying 44 bits of entropy is not enough. the whole point of the comic is, that 4 words out of a list of 2000 is more secure then some shorter password with leetcode and a number and punctuation at the end. which feels rather intuitive given that 4 words are way easier to remember
While this comic is good for people that do the former or have very short passwords, it often misleads from the fact that humans simply shouldn't try to remember more than one really good password (for a password manager) and apply proper supplementary techniques like 2FA. One fully random password of enough length will do better than both of these, and it's not even close. It will take like a week or so of typing it to properly memorize it, but once you do, everything beyond that will all be fully random too, and will be remembered by the password manager.
The part where this falls flat is that using dictionary words is one of the first step in finding unsecured password. Starting with a character by character brute force might land you on a secure password eventually, but going by dictionary and common string is sure to land you on an unsecured password fast.
Even if an attacker knew that your password was exactly four words from a specific list of only 2048 common words, that password would still be more secure than something like Tr0ub4dor&3
https://www.explainxkcd.com/wiki/index.php/936:_Password_Strength
No, it would not. 2048 to the power of 4 is significantly less than 60 to the power of 11.
https://www.wolframalpha.com/input?i2d=true&i=Power%5B2048%2C4%5D%E2%80%94Power%5B60%2C11%5D
That's true but in practice it wouldn't take 60^11 tries to break the password. Troubador is not a random string and all of the substitutions are common ( o -> 0, a ->4, etc. ). You could crack this password a lot easier with a basic dictionary + substitution brute force method.
I'm saying this because I had an assignment that showed this in an college cybersecurity class. Part of our lesson on password strength was doing a brute force attack on passwords like the one in the top of the xkcd meme to prove they aren't secure. Any modern laptop with an i5 or higher can probably brute force this password using something like hashcat if you left it on overnight.
Granted, I probably wouldn't use the xkcd one either. I'd either want another word or two or maybe a number/symbol in between each word with alternating caps or something like that. Either way it wouldn't be much harder to remember.
Troubador is not a random string
except it is not troubador. it is troubador, ampersand, digit.
if you know there are exactly two additional characters and you know they are at the end of the string, the first number is really slightly bigger (like 11 times)
once the random appendix is 3 characters or more, the second number wins
https://www.wolframalpha.com/input?i2d=true&i=Divide%5BPower%5B2048%2C4%5D%2CPower%5B256%2C3%5DPower%5B2%2C4%5D4*500000%5D
and moral of the story is: don't use xkcd comic, however funny it is, as your guidance to computer security. yes, the comic suggestions are better than having the password on a post-it on your monitor, but this is 21st century ffs, use password wallet.
That'd why words are from the eff long word list and there are 6 words
then someone uses a dictionary attack and your password gets cracked within minutes
see, you didn't get the whole comic. 4 words out of a dicitionary with 2000 words has more combinations then a single uncommon non gibberish baseword with numeral and puction at the end. as long as the attacker knows your method.
a dicitonary attack will not lower the entropy of 44 bits, thats what the comic is trying to say
It the length not the content for the most part. Some keys have syntax such as leading or trailing characters.
While the joke is funny, what is the context? Why did she post the original tweet in the first place?
It's lady gaga.
If you've followed her at all, even indirectly, this is NOT the weirdest thing she's done, and bluntly, the weirder stuff wasn't justified (to the public at least).
I'm not trying to throw shade at Gaga at all. Lady, let your freak flag fly all day long. You don't need my permission to do it, but if you want it, you got it. Weird isn't bad, it's just weird.
IMO, at this point, gaga doesn't need a reason to be weird.
I don't follow her at all so thanks for the explanation!
I would not have thought that she knows what a private key is 🙉 humans and their prejudices…
Ohhh, it is the other way around, gaga‘s tweet is older
I genuinely LOL'd at this thank you OP.
lol