Well that was an approximation to keep it simple and disprove the given example. There are other directories in the root filesystem that are in the path by default, or used in some other critical way (like /etc). Even if they are links to directories in the nix store you can replace the link.
ivn
These seems to be related to flatpak, not immutability.
What things?
What namespace are you talking about?
To be honest I don't know these very well. I only use NixOS. My understanding is that in an immutable distribution the root filesystem is read-only. Granted in NixOS the nix store is immutable and most things in the root filesystem are just links to the nix store, but the root filesystem itself is not read-only.
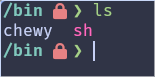
I'm on NixOS right now and just dropped a Chewy in my /bin, only had to sudo touch /bin/chewy.
if it's being read from, it can be written to.
Why would being able to read imply being able to write?
Having an extra step or two in the way doesn't make it "extremely secure".
Well it can greatly improve security by preventing a compromised app to achieve persistence.
The store is immutable but the system itself definitely isn't.
I wouldn't call NixOS immutable.
Mais c’est pas un black-list (comme le serait l’insance nsfw ou sci-hub, juste une URL qui ne résous pas)
Pourquoi est-ce que tu penses que ce n’est pas le domaine qui est bloqué ?
void( ... ) c’est une fonction particulière de Javascript, je pense qu’ici c’est utilisé pour que le reste soit exécuté immédiatement (et non pas considéré comme une déclaration pour plus tard)
Normalement le contenu de la page est remplacé par le résultat de l’évaluation du javascript, sauf si le résultat est undefined, void() renvoi undefined.
Yes, some toolchain expect you to run pre-compiled dynamically linked binaries. These won't work on NixOS, you need to either find a way to install the binary from nix and force the toolchain to use it or run
patchelfon it somehow.