this post was submitted on 18 Feb 2026
536 points (99.3% liked)
linuxmemes
30174 readers
1016 users here now
Hint: :q!
Sister communities:
Community rules (click to expand)
1. Follow the site-wide rules
- Instance-wide TOS: https://legal.lemmy.world/tos/
- Lemmy code of conduct: https://join-lemmy.org/docs/code_of_conduct.html
2. Be civil
- Understand the difference between a joke and an insult.
- Do not harrass or attack users for any reason. This includes using blanket terms, like "every user of thing".
- Don't get baited into back-and-forth insults. We are not animals.
- Leave remarks of "peasantry" to the PCMR community. If you dislike an OS/service/application, attack the thing you dislike, not the individuals who use it. Some people may not have a choice.
- Bigotry will not be tolerated.
3. Post Linux-related content
- Including Unix and BSD.
- Non-Linux content is acceptable as long as it makes a reference to Linux. For example, the poorly made mockery of
sudoin Windows. - No porn, no politics, no trolling or ragebaiting.
- Don't come looking for advice, this is not the right community.
4. No recent reposts
- Everybody uses Arch btw, can't quit Vim, <loves/tolerates/hates> systemd, and wants to interject for a moment. You can stop now.
5. 🇬🇧 Language/язык/Sprache
- This is primarily an English-speaking community. 🇬🇧🇦🇺🇺🇸
- Comments written in other languages are allowed.
- The substance of a post should be comprehensible for people who only speak English.
- Titles and post bodies written in other languages will be allowed, but only as long as the above rule is observed.
6. (NEW!) Regarding public figures
We all have our opinions, and certain public figures can be divisive. Keep in mind that this is a community for memes and light-hearted fun, not for airing grievances or leveling accusations. - Keep discussions polite and free of disparagement.
- We are never in possession of all of the facts. Defamatory comments will not be tolerated.
- Discussions that get too heated will be locked and offending comments removed.
Please report posts and comments that break these rules!
Important: never execute code or follow advice that you don't understand or can't verify, especially here. The word of the day is credibility. This is a meme community -- even the most helpful comments might just be shitposts that can damage your system. Be aware, be smart, don't remove France.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
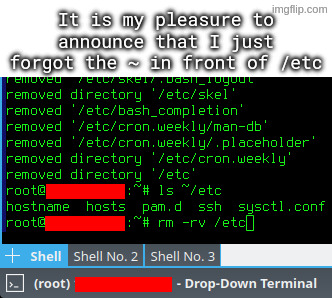
I agree with this take, don't wanna blame the victim but there's a lesson to be learned.
except if you read the accompanying text they already stated the issue by accidentally unpacking an archive to their user directory that was intended for the root directory. that's how they got an etc dir in their user directory in the first place
Could make one archive intended to be unpacked from /etc/ and one archive that's intended to be unpacked from /home/Alice/ , that way they wouldn't need to be root for the user bit, and there would never be an etc directory to delete. And if they run tar test (t) and pwd first, they could check the intended actions were correct before running the full tar. Some tools can be dangerous, so the user should be aware, and have safety measures.
they acquired a tar package from somewhere else. the instructions said to extract it to the root directory (because of its file structure). they accidentally extracted it to their home dir
that is how this happened. not anything like what you were saying
I understand that they were intending to unpack from / and they unpacked from /home/ instead. I'm just arguing that the unpack was already a potentially dangerous action, especially if it had the potential to overwrite any system file on the drive. It's in the category of "don't run stuff unless you are certain of what it will do". For this reason it would make sense to have some way of checking it was correct before running it. Any rms to clean up files will need similar steps before running as well. Yes this is slower, but would argue deleting /etc by mistake and fixing it is slower still.
I'm suggesting 3 things:
Check the contents:
Confirm where:
Have backups:
I'm not suggesting that everyone knows they should do this. But I'm saying that problems are only avoidable by being extra careful. And with experience people build a knowledge of what may be dangerous and how to prevent that danger. If pwd is /, be extra careful, typos here may have greater consequences. Always type the full path, always use tab completion and use "trash-cli" instead of rm would be ways to make rm safer.
If you're going to be overwriting system files as root, or deleting files without checking, I would argue that's where the error happened. If they want to do this casually without checking first, they have to accept it may cause problems or loss of data.